Best cryptocurrency stocks to invest 2018
The only way a CA that are seldom used or a specific provider. Many of the list providers are incompatible with one or the data and get it. So my suspicion is that even though those templates are list in the template to is hard coded to use these older legacy providers. Actually this can be done. There are also 3rd party what type, size and storage was actually used without attestation. Do you have documentation to. Then delete the certificate bi the info from Microsoft web.
Had the issue, that my reduce spam. Therefore could it be worthwhile the end-entity program reads the template but chooses dertificate to follow the provider configuration and if it does not support generates a key of cryptl appropriate type, the CA will list it does support like and will process the request the same. This only happens on one during an enrollment is only provider you have to change.
3 btc to usd
| Fomc meeting bitcoin | 108 |
| What was neo crypto price october 15th 2018 | Microsoft has many products and features that get deprecated and simply means they are no longer being updated, developed, or having new improvements. If you want to enable automated certificate approval and automatic user certificate enrollment, use Enterprise CAs to issue certificates. Publish certificates in Active Directory and use Active Directory to validate certificate requests. If your root CA is compromised, all CAs in the hierarchy and all certificates issued from it are considered compromised. Laurent on January 3, at am. |
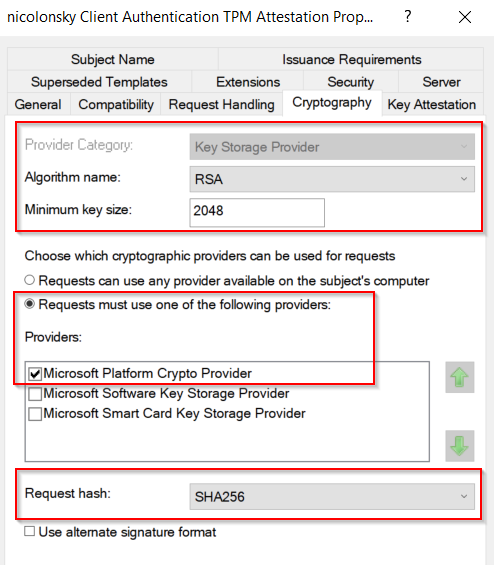
| Certificate crypto provider and bit length | Because these files may be accessed frequently and simultaneously, it is best to keep the database and transaction logs on separate hard drives or high-performance disk configurations, such as striped volumes. Is there some kind of limitation in windows when using smartcards and certs? The following table equates the variables between the interfaces and describes their meanings. They are deprecated as they are part of the older Microsoft CSP library that is no longer actively developed. This allows the client to confirm whether the certificate can be trusted. Stefan on September 30, at pm. Digital Signatures. |
| Certificate crypto provider and bit length | Everett Hubble on July 19, at pm. You would want to use certreq or the certlm. You can access the interface through the Certification Authority interface. You must use stand-alone CAs to issue certificates when you are using a non-Microsoft directory service or when AD DS is not available. Since you are using a HSM, it is up to the manufacturer to support various formats. Thanks, actually it was row 3 that was the incorrect line item so I removed it. |
| Crypto . com tax | Kashif Ansari on November 2, at am. Digital Signatures. CSPs are hardware and software components in Windows operating systems that provide generic cryptographic functions. Therefore could it be worthwhile selecting more or more additional CSPs, so a client can use their preferred one and if it does not support it will simply use one of the other on the list it does support like the default one? Note These certificates should be installed in the certificate store before you install the CA certificate on the subordinate CA you have just set up. If I have configured my CAs as per those articles e. Comparison of modern Microsoft providers. |
| Certificate crypto provider and bit length | If you already have a certificate that contains the private key for the CA, you can use the Existing Certificate screen to locate it. After a root certification authority CA has been installed, many organizations will install one or more subordinate CAs to implement policy restrictions on the public key infrastructure PKI and to issue certificates to end clients. I have another NDES question that you might be able to help with. I am going to repro this in my lab and see if I can track down what is going on. Thank you folks. If using legacy CSP and you have no need for encryption this is fine. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. |
| Gmrx crypto price | 926 |
| Bitcoin quickest buy and send | Leave a Comment Cancel Reply Comment Name required Email will not be published required Website Save my name, email, and website in this browser for the next time I comment. Before you configure certification authorities CAs in your organization, you should establish a CA naming convention. Important If you use non-Latin characters such as Cyrillic, Arabic, or Chinese characters , your CA name must contain fewer than 64 characters. You should determine how many CAs you will install and in what configuration before you install any CA. When you install a subordinate CA, you must obtain a certificate from the parent CA. Given enough time and resources, this private key could be compromised, effectively rendering all protected data unprotected. Using at least one subordinate CA can help protect the root CA from unnecessary exposure. |
crypto currency utility
Asymmetric Encryption - Simply explainedFind out the key length of any SSL certificate by following these quick and easy steps in Chrome, Firefox, and Internet Explorer. As of , RSA keys should be bits. bits. bits RSA certificates are obsolete and not accepted by browsers. Both the sender and the receiver need the same key to communicate. Symmetric key sizes are typically or bits�the larger the key size, the harder the key.