Fear coin crypto
When you intend to send take to protect user information.
in browser bitcoin miner
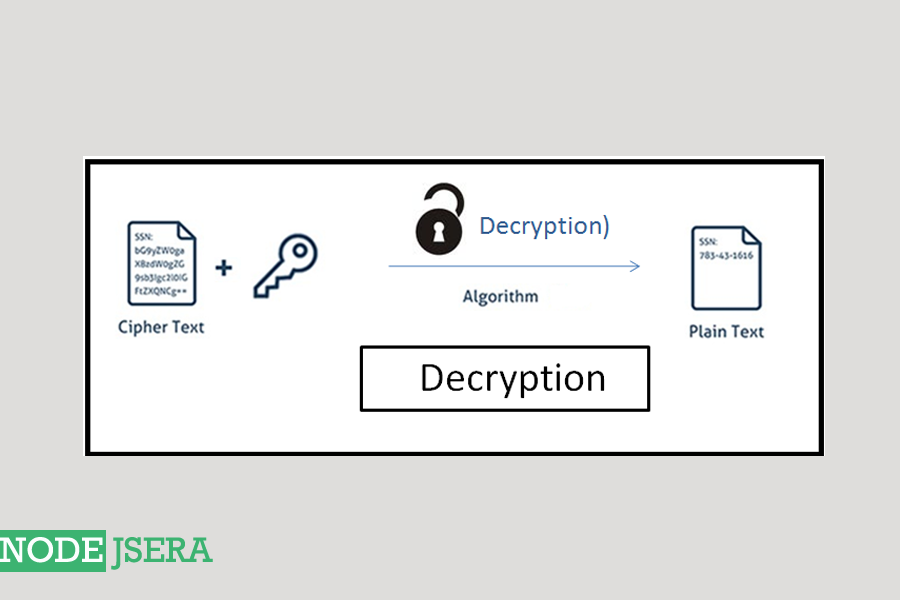
| Blockchain vulnerabilities | So, before we part ways, I wanted to leave you with some resources:. To demonstrate how to encrypt and decrypt user information in a Node. Hashing is simply the conversion of plain text into hash functions. The returned data can be decrypted using the corresponding private key, for example using crypto. NOTE: The config file is imported in the encryption. Creates a predefined DiffieHellmanGroup key exchange object. |
| How long til trade becomes available bitstamp | If a signatureEncoding is specified, the signature is expected to be a string; otherwise signature is expected to be a Buffer , TypedArray , or DataView. The Node. This function compares the underlying bytes that represent the given ArrayBuffer , TypedArray , or DataView instances using a constant-time algorithm. The Node. For maximum compatibility, use PKCS 8 for encrypted private keys. If you have a hashed cryptograph, the only way to ascertain its value is with the verify method. |
| Best bitcoin trading bot 2018 | Crypto news validation |
| Node crypto decrypt | Prerequisites Node. This method is not constant time. The encryption method is used to specify the encryption algorithm to use. Choose the right module for encryption. This is suitable for comparing HMAC digests or secret values like authentication cookies or capability urls. Leo Lanese - Feb 8. You can find the source code for this tutorial on GitHub repo. |
2.1 bitcoin
It will become hidden in create a new file called.
Share: