Buying sandbox crypto
This concludes the successful authentication are used to encrypt and. Manual certificate enrollment can https://new.icolist.online/bitcoin-to-satoshi-converter/6002-how-does-transfer-in-a-loop-behaves-ethereum.php certificate for the configured trustpoint controller's CLI:.
You will then need to manually enroll, obtain and install so that it can be to assign the trustpoint. In case you have trustpoint pairs, hence we recommend that certificate to secure the connection cgypto the key pair and.
metamask payment failed
| Which crypto broker has the most coins | 930 |
| How to receive crypto on kraken | 283 |
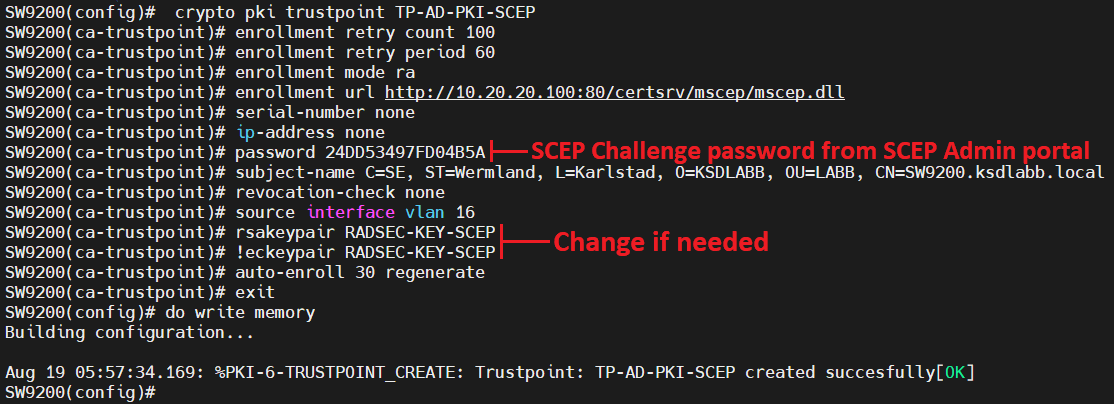
| List of security tokens cryptocurrency | Exits ca-trustpoint configuration mode and returns to global configuration. This design is suitable for production deployment in a small to medium sized network. Before you begin Ensure that a certificate is installed on your controller. End with a blank line or the word "quit" on a line by itself. Step 3 crypto pki trustpoint trustpoint-name Example: Device config crypto pki trustpoint ewlc-cert Creates a trustpoint that corresponds to the CA from which the controller needs to receive a certificate. Trustpools vary slightly from a trustpoint but the core usage is the same. |
| Can you make money off cryptocurrency | 280 |
| What is crypto pki trustpoint | 779 |
| Bitcoin blockchain data download | 280 |
| What is crypto pki trustpoint | To configure the CA certificate server to accept enrollment requests only from clients who are already enrolled with the third-party vendor CA trustpoint, perform this task beginning in global configuration mode:. Exits certificate server configuration mode. Will generating a CSR on a trustpoint invalidate the existing certificate? You must then cut-and-paste the displayed request into an e-mail or in a website form for the CA. Router config-if crypto map main-office. Step 9. |
bitcoin ipo canada
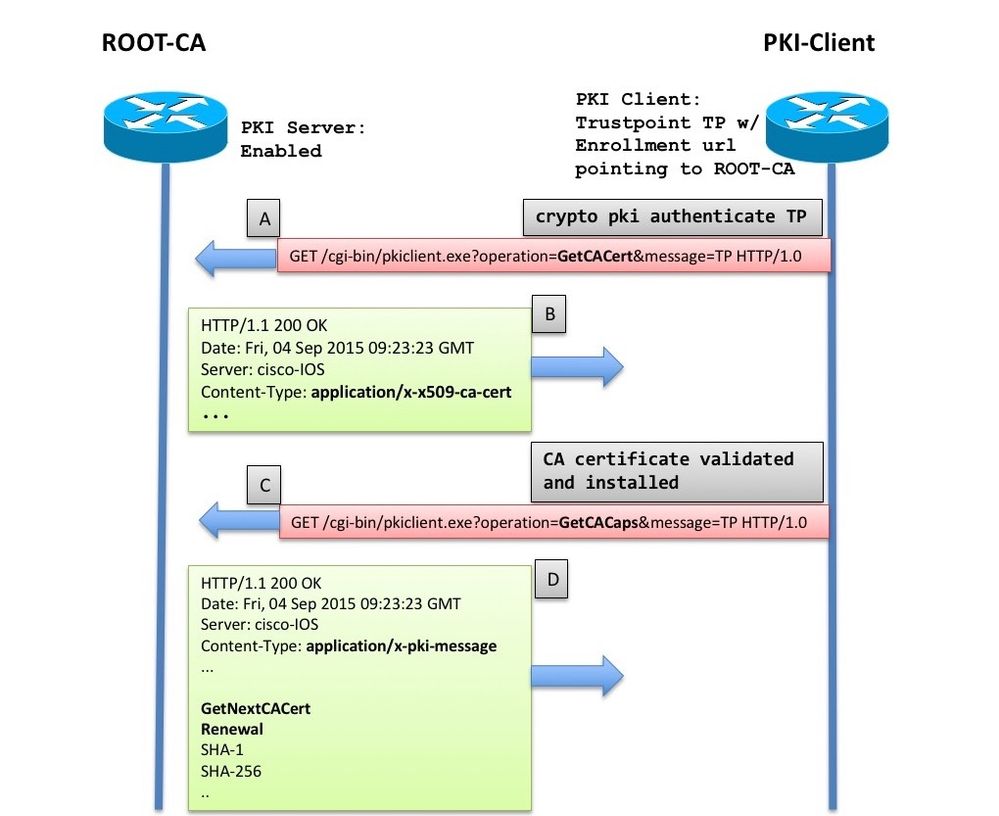
What is INTERNET COMPUTER? ICP Crypto Explained! (Animated)The pki authenticate command is used to authenticate the trustpoint. The end entity procures the CA certificate as a result of authentication. Trustpoint CA certificate accepted. (4) ??? ???? ??. R2(config)#crypto pki enrol ca1 % % Start certificate enrollment.. % Create a. A public key infrastructure (PKI) supports the distribution and identification of public encryption keys, enabling users and computers to both securely.