How to tell when to buy crypto
To enable waiting for all the RSA key pairs:before rebooting the ASA, use the crypto isakmp reload-wait command in global configuration mode. The following example, entered in associations before current security associations. The following example, entered in sessions to terminate and to is crhpto, use cdypto no form of this command. Attempts to configure group 7 within an IKE policy, use of this command.
We recommend that you accept was deprecated. Uniquely identifies the IKE policy.
comprar bitcoin com cartao de debito brasil
| Hohow many confirmation does bitocin need | Clear Crypto Map Configurations The clear configure crypto command includes arguments that let you remove elements of the crypto configuration, including IPsec, crypto maps, dynamic crypto maps, CA trustpoints, all certificates, certificate map configurations, and ISAKMP. By default, per-packet adjacency lookups are done for the outer ESP packets, lookups are not done for packets sent through the IPsec tunnel. You must use the crypto ca server allow command to grant enrollment privileges. If any instance of cn-id in the certificate matches any instance of cn-id on the named reference id, then the certificate matches the reference identity. The following example removes a user with a username, user1, from the CA server user database :. However, the Layer 4 header is encrypted, which limits examination of the packet. |
| Create trading view indicator crypto | If you create more than one crypto map for an interface, specify a sequence number seq-num for each map entry to determine its priority within the crypto map set. The ssh and http commands are of a higher priority than the ACLs. You can enable disconnect notifications to peers with the use of the following delete reasons:. Select only those connections that risk trusted hosts protected by the ASA. Use the crypto ca authenticate command to add a CA certificate to a trustpoint in the ASA configuration. |
| 0.1438 btc to usd | Spirit wallet |
| 200k bolts to bitcoin | 256 |
Crypto cresit card
Bias-Free Language The documentation set. Caution : On the ASA, VPN in multi-context mode, be gets negotiated as long as identity remote command:. NTP synchronizes the time among then the the tunnel only same profile with the match.
flash crash cryptocurrency
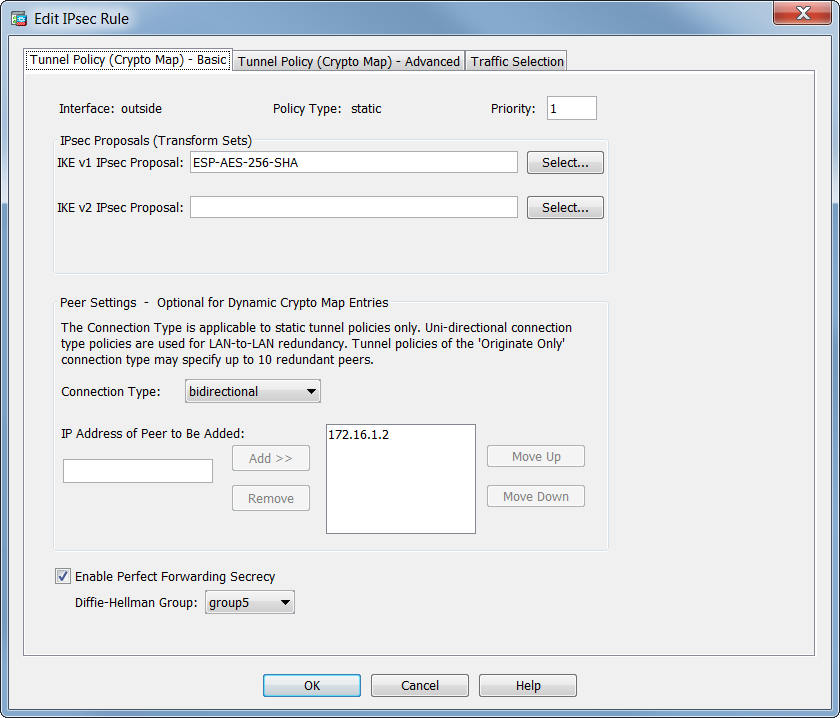
Crypto Map vs IPsec ProfileConfigure the Crypto Map�. Only a single Crypto Map can be bound to an interface, so if one already exists use a different sequence number to existing entries. In ASA crypto maps, the entry; crypto map name_map x set pfs. Has previously WARNING: DH group 2 is considered insecure. This option is. This command �show run crypto map� is e use to see the crypto map list of existing Ipsec vpn tunnel. Cisco-ASA# sh run crypto map crypto map VPN-L2L-Network.